Alongside the coronavirus pandemic, cyber attackers are having a field day with malicious mails, messages and websites disguised as health advisories.
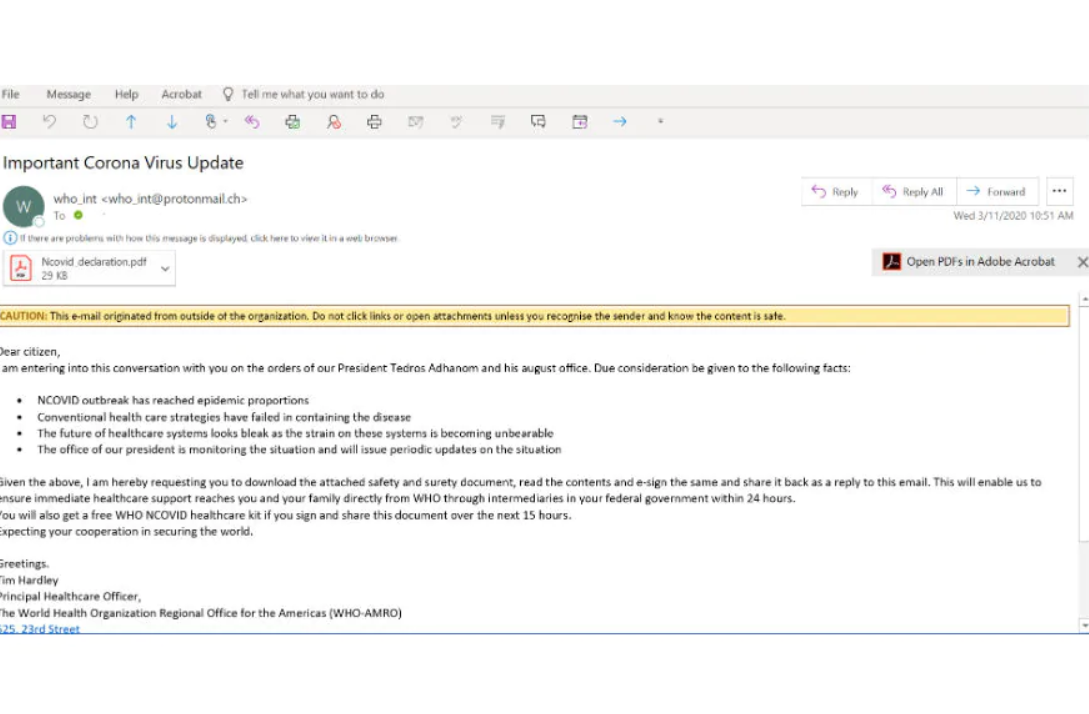
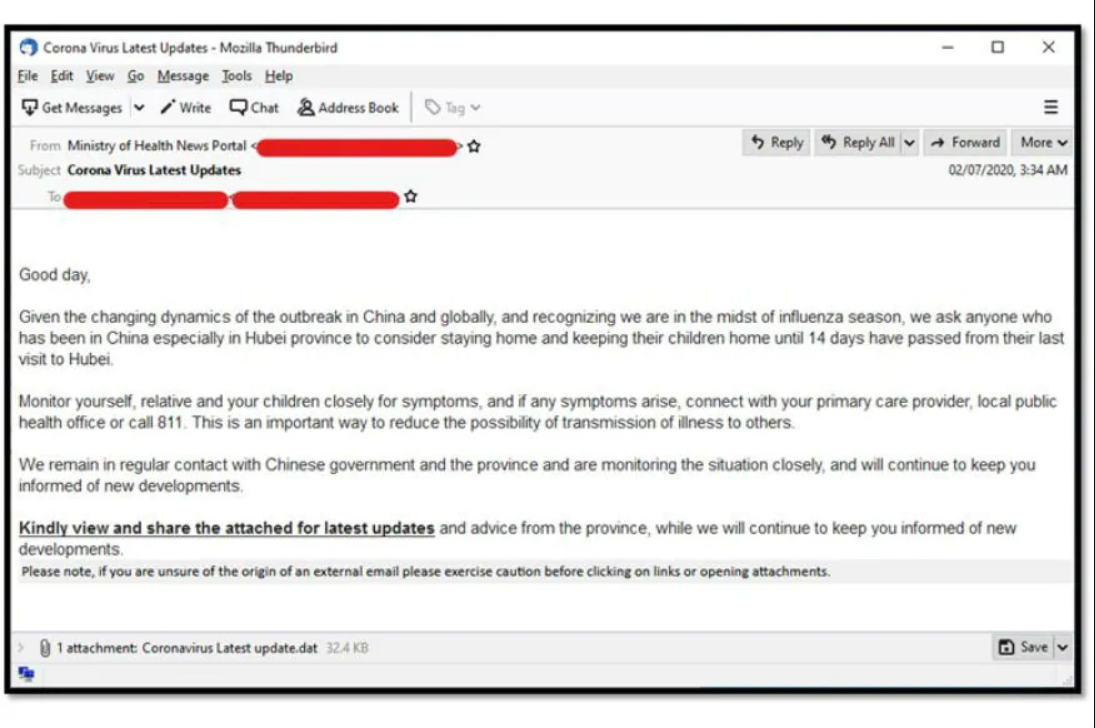
The coronavirus pandemic is causing global lockdowns of bustling metropolitans, with scientific laboratories working overtime to come up with enough testing kits, potential cures and a future vaccine. While such actions are underway, cyber attackers across the world are having a field day by cashing in on the global panic that the virus has caused. The result is a wide range of phishing messages and malware-ridden emails that pretend to be healthcare directives from the World Health Organisation (WHO) or other global or national healthcare organisations, all with one purpose — steal your money and data.
Alongside malware, the key intent is to sell fake cures and peddle mass hysteria through fake news.
ESCALATING NUMBERS
Speaking to News18 on the matter, Himanshu Dubey, director of Quick Heal Security Labs, stated that the approach of the attackers have been threefold. He says, “Attackers always look out for trends, and are fluent at that. Based on the data that we’ve seen, several thousands of new websites are coming up every day. The key intent is to deliver malware, or sell fake cures and vaccines to scam people of money, and thirdly, targeting fake news to peddle mass hysteria.”
The 15 Most Common Scams Thieves Use To Con People Are Hiding Right In Plain Sight
The attacks also seem to be steadily on the move. As Dubey reveals, “A couple of weeks ago, the number of new (malicious) domains spotted everyday was close to 1,000, whereas recent observations from a couple of days ago saw that the number of new URLs is close to 10,000.”
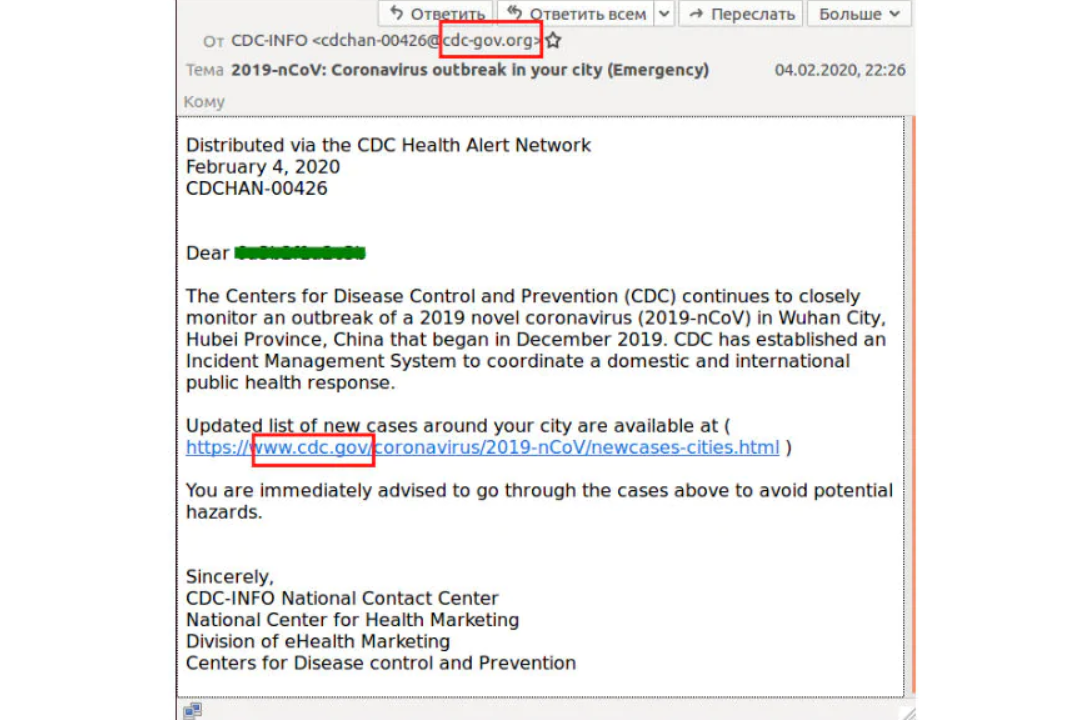
Kiran Zachariah, vice president of the IoT business division at Subex, shared some data with News18 that clearly reflected on the escalating nature of these attacks. “In the week ending February 8, we saw just three instances of such (phishing and malware) emails, which rose to 42 in the week ending March 14. The variation in attribution has also changed along with messaging clusters — last week, we saw 22 emails attributed to the WHO, 12 to the United States CDC, and three each to the MoHFW India, the Government of India and NHS UK. The rest were attributed to a supposed ‘emergency team from the United Nations’,” added Zachariah.
The malware they put in your system now can later infect your entire office network when normalcy returns.
HOW THEY ATTACK
The process of the attacks, as industry experts state, have remained consistent with previous behaviours of cyber criminals, but have simply evolved in precision and sophistication. As Dubey says, “Most of the malware that users are receiving (through emails, websites or software) are information stealers. These tools primarily try to steal browser databases of users, where many store email passwords, social media details and even financial credentials. In certain cases, we have also noticed remote access tools (RATs) being deployed, which can give the hackers access to individual devices, remotely. In still more, ransomware are directly employed.”
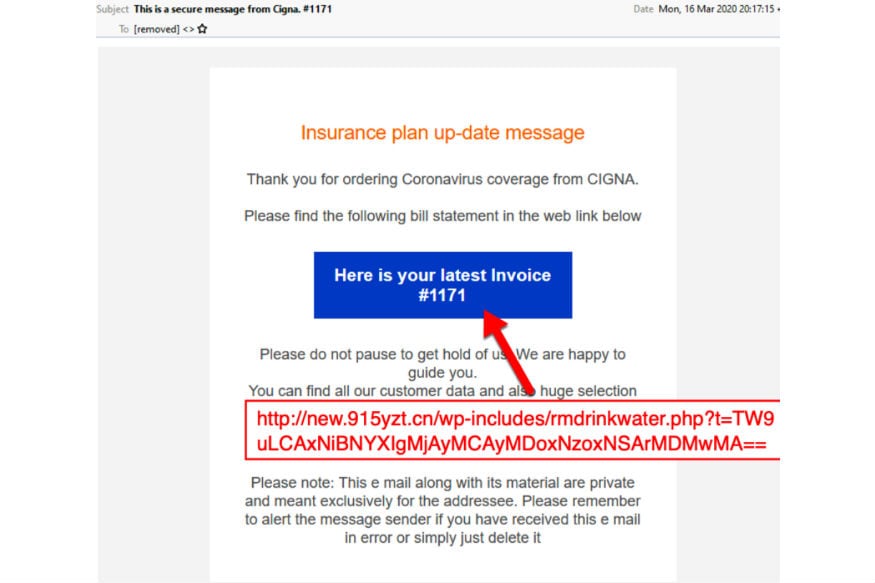
Dubey further affirms that these attackers, when going about spreading malware related to coronavirus, are showing greater levels of sophistication than before. “Attackers are using updated, accurate data on their sites and tools from actual health organisations. Previously, such sites were largely or identifiably fake. With COVID-19, we have noticed that even the scam sites update info as soon as a nation releases official data,” he says.
Dubey confirms that such an approach is particularly useful in a country like India, which with its massive population and diverse demographics give the attackers a sizeable target. With over 1.3 billion individuals in the country, and large volumes of individuals coming online every month, India has a large number of people who access the internet without proper education, which in turn exposes them to websites such as those mentioned above, hence amplifying the risk. Many in India are far from being tech savvy, which makes it difficult for them to understand the fine differences between a fake URL, and a real one.
Apple offers modified phones to security researchers looking for iOS weaknesses
Subex’s Zachariah interestingly projects that through these attacks, cyber criminals are actually creating a scope to amplify hacks in future. As he says, “Some of these infected devices can be used to attack secure infrastructures that they connect to later. For instance, if you click on a link and infect your laptop while working from home, the infection could spread and create a larger problem when you take your laptop back to the office, and connect to the Wi-Fi network there.”
Along with the issues of the attacks being more authentic in appearances and running dormant in the background, Zachariah states that quite often, it is very difficult to even know that a machine has been infected. “Sometimes, such infections do not hamper the normal operations because most of the (devices) come with good compute power. This was not so about seven years ago, when malware infections would slow down devices so much that the OS had to be reinstalled.”
The on-ground situation is often masked due to people not reporting cyber crimes frequently enough in India.
As of now, cyber attacks using coronavirus as bait have been running relatively unchecked in India, due to the lack of people reporting about them as of now. As Prof. Triveni Singh, superintendent of police at Azamgarh, and head of Uttar Pradesh Police’s cyber crime special task force, states that the lack of official complaints (for obvious reasons) may be the key reason why such attacks are steadily increasing in India.
Japan, Britain to protect encryption keys in trade pact, Nikkei says
As Singh states, “Official reports on these attacks are only filed once individuals face some concrete or financial losses. As a result of this, cyber criminals do many illegal online activities in India, but because of the lack of official complaints due to no financial losses, we often don’t get to know the on-ground scale of these attacks. For instance, many people do not report cyber crimes such as login thefts, and contacts or email thefts. No one really goes to the police as long as their money is not stolen.”
Singh further affirms that India has a long way to go in terms of reportage of cyber crimes, and urges individuals to come forward and seek help with the police in cases of online frauds and attacks, even in situations where no money is lost. He told News18 that while some of the most reported cases are UPI frauds and ransomware crimes, they are only a part of the total volume of cyber attacks in India.
News18 / Balkantimes.press
Napomena o autorskim pravima: Dozvoljeno preuzimanje sadržaja isključivo uz navođenje linka prema stranici našeg portala sa koje je sadržaj preuzet. Stavovi izraženi u ovom tekstu autorovi su i ne odražavaju nužno uredničku politiku The Balkantimes Press.
Copyright Notice: It is allowed to download the content only by providing a link to the page of our portal from which the content was downloaded. The views expressed in this text are those of the authors and do not necessarily reflect the editorial policies of The Balkantimes Press.

